Welcome back to our fifth article from The Cyber Blog Times Edition. Today, we discuss security automation.
Without further ado, let’s see what security automation consists of. It consists of using technologies to perform tasks, with reduced human effort, to integrate processes, applications, and security infrastructure.
5 ways to implement Security Automation
For most companies, security is a major concern. Traditional security approaches are often in conflict with agile methodologies for application development and DevOps practices. However, successful implementation of DevSecOps can be difficult due to the difficulty of bringing together security, development, and operations teams.
Automation is key to a successful DevSecOps initiative. This checklist covers five ways Excellium Services can help you get started.
1. Make processes and workflow resilient and reusable
Automating workflows and processes make them more understandable by the user. It will increase productivity considering that the long and complicated tasks that hinder the flow are now easy and require only a few inputs.
It also facilitates the share of good practices and collaboration between your teams.
How does security automation avoid human errors?
Common use case:
Alice wants to create a new VM and open a NAT rule on a firewall.
- Without DevSecOps:
Alice should make 2 change tickets in the ITSM tool.
The first one, for the VM giving identification variables on the creation form such as hostname, subnet, vlan etc… Then, Bob must create the VM with the specified information.
The second one, for the NAT rule. Alice must give information about the port number, which firewall the rule must be open, network information for the VM etc… Then, Bob must check that the change request is standard and secure. If not, it will go through another ITIL process i.e. CAB, Security compliance etc…
- With DevSecOps:
Alice will use an automated CI/CD pipeline that has been versioned and tested and follows Security Automation best practices from Excellium.
This pipeline is connected to any referential that are part of the organization (IPAM, CMDB…). Through API calls, it will gather the mandatory information and provide feedback after every
successful step.
Here, Bob’s role is really limited since he will just have to validate the pipeline execution.
2. Involve teams towards a common goal
DevSecOps brings development, security, and operations teams toward a common goal (Security Automation). As they share the responsibility for the project outcome, it enhances collaboration and synergies. When Developers and Operations used to talk only by vertical escalation, DevSecOps facilitates the exchange between teams by means of ChatOps tools and lets your teams organize themself in a horizontal manner.
Without the fear of failing and sharing knowledge, individuals are continuously evolving and learning, the results are:
- Improving self-confidence,
- Limiting Single Point of Failure ( SPoF ),
- Increasing productivity,
- Improving the quality of work.
3. Secure by design
When building an automation process from the DevSecOps point of view, we design it to be secure at every step. From development to delivery and operations, we add tools that enforce security.
Pipelines are made to fail fast in order to indicate quickly to developers and operations where to fix problems when occurred. It also ensures backward compatibility and non-regression.
Along the pipeline, “test-driven development tools” and “behaviour-driven development tools” are here to assure the adequation of the development with the product features that are defined by the Product Owner.
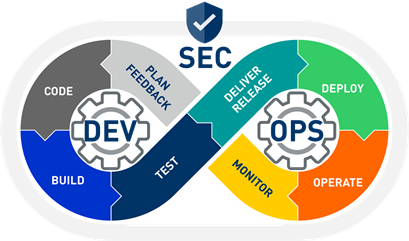
In Lehman terms, Security Automation consists of implementing the right tools at the right moment of the DevSecIos chain (see figure 1).
4. Use the 3 ways of DevOps
The philosophy behind the 3 ways makes sure that feedback and continuous improvement are followed.
- By Automating workflows, feedback is easy as the pipeline executions are monitored into the CI/CD tool. As most of the CI/CD orchestrators have API/Webhooks capabilities, you will never lose track of deployment or new releases. Indeed, every critical event will be transmitted to ChatOps tools such as Teams, Slack or email.
- As the pipeline has been built with the help of several teams, knowledge is spread among many people letting them know where it failed. It will also shorten the recovery time and improve reliability, thus security.
- Usually, adopting an automation process is not done overnight. It takes time to refine the pipeline. Starting small will already have an impact on Time to Market (TTM).
As you deepen into Security Automation, you will start failing more and more. The more you fail, the more your pipeline will be resilient. Indeed, security is not a simple task and sometimes taking risks through experimentation lets you discover new things that you did not see before.
5. Cloud Agnostic approach for easy scaling
With the usage of containers technologies and public cloud “Point of Presence”, we are now able to seamlessly migrate applications to the cloud. Moreover, using new Infrastructure-as-Code tools we can easily create IaaS, PaaS on any public/private/on-premises cloud.
In this way, we enforce the availability and reliability of your most critical applications.
Finally, from a business point of view, in the case of high-density traffic due to marketing events and such, the power of the cloud let you scale the number of instances in order to keep a constant Quality of Service ( QoS ) for all your clients, which will greatly improve the customer experience.
Ready to test your Security Automation knowledge?
You didn’t think you could quit the reading without playing the quiz, did you?
- According to you, what could be 3 benefits for implementing DevSecOps in your team? (Open answer).
- What kind of threat DevSecOps and Security Automation is capable of avoiding?
- Credentials in source code
- Malicious software in the container image
- Man-in-the-Middle attacks
- Infrastructure alteration for future infiltration
Did you enjoy this Security Automation-oriented reading?
Don’t hesitate to let us know and share it with your friends!



